Every website owner's biggest concern is securing a managed WordPress hosting website.
According to research by w3techs in March 2019, WordPress is by far the most popular Content Management System (CMS). 60.4% of websites that use a CMS use WordPress, or around 3.5% of all websites.
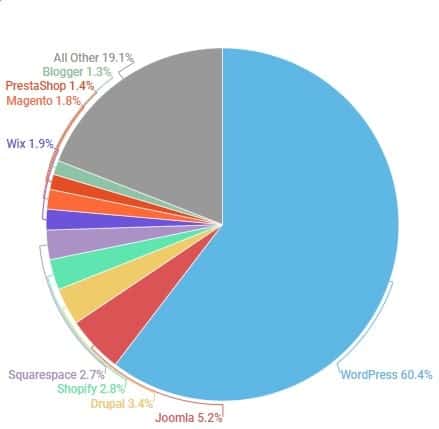
That means that there are millions of website owners concerned about securing their managed WordPress hosting. You've probably heard the myth that WordPress sites experience a lot of attacks and hacking opportunities because WordPress isn’t secure, but the likeliest reason is simply down to the numbers. WordPress has more reported security issues and hacked websites because it makes up such a large percentage of CMS hosted websites. This gives more incentive for hackers to search for security flaws and exploits in WordPress websites, because they have so many more potential targets.
WordPress, as a system, and especially its core files, are highly secure. They are regularly maintained and frequently updated by hundreds of programmers who are part of the open-source WordPress community. Actually, a significant proportion of WordPress security problems usually result from human error, like a managed WordPress hosting site that wasn't configured currently or WordPress sites updates that were poorly maintained.
Migrate to uPress within 24 hours
In this guide we'll discuss the best maintenance and security advice for securing your managed WordPress hosting website.
WordPress Security should be taken seriously
Fun Fact – On a weekly basis Google adds more than 20,000 websites to their blacklist for malicious content, and more than 50,000 websites for phishing.
* This guide is aimed at WordPress websites hosted on a Linux server, but maybe relevant for managed WordPress hosting on Windows servers as well.
This section is aimed at website owners using managed WordPress hosting or who are handling their own WordPress site management, and want to set everything up with the greatest possible level of security.
When your site uses managed WordPress hosting, you're benefiting from the large community of dedicated web developers who keep WordPress free and open-source. The CMS may look like a single unit, but it's actually made up of two main components:
The immense success of WordPress generated a huge plugins and themes repository, made by third-party developers and companies worldwide. These plugins connect to your core WordPress site, adding features and functionality to your managed WordPress hosting site
WordPress has tens of thousands of plugins and themes. It's crucial to choose ones which are actively managed, with owners who regularly release updates and provide support. Just like core WordPress updates, plugin and theme updates help fix known security issues, close loopholes that hackers could exploit, and make sure that your site is as secure as possible. An old plugin that no longer receives active support is an open door for hackers.
* A note on premium/paid plugins and themes that are not available through the WordPress plugin repository:
Paying for a plugin or theme outside of the WordPress plugin market does not guarantee its quality and security. All too often, these premium plugins and themes aren't updated regularly, or at all. Even when they are updated, the process is usually complicated and has to be done manually.
We highly recommend using only plugins and themes from the official WordPress plugin repository that were developed by well-known companies and are kept updated, for your managed WordPress hosting or self-hosted site. This will go a long way to preventing any security issues, since these plugins and themes were thoroughly checked to make sure they don’t contain any malicious code, and are kept in line with security issues.
It’s crucial to pick a secure username for your managed WordPress hosting or self-hosted website. If you use "admin" as your username, you are basically doing half the job for hackers targeting your website.
This is probably one of the most important and easy steps you can take to secure your website and prevent unnecessary risks.
A Brute Force attack is one of the most common hacking methods. It's when hackers just try out hundreds of passwords, hoping that they'll get lucky and hit on the one you used for your account. The harder it is to guess your password, the less likely it is that this kind of attack would succeed.

Astrovector / Shutterstock
That’s why it's so important to create a long and complicated password for your website. When we say "for your website," we mean your WordPress dashboard, your FTP accounts, databases, WordPress managed hosting, the email you use to recover your site, and anything else tied to your website. If you’re using managed WordPress hosting, make sure that you generate a different unique password for every account.
There's a surprising number of WordPress users that use phrases such as "password" or "12345678" as their password. These passwords, along with birth dates, ID numbers, and phone numbers, are easy to guess and will be among the first that bots or hackers will try.
Many website owners don't like to use long and complicated passwords simply because they're hard to remember. A good solution is to use a complete sentence that makes sense only to you (and even misspelling a word on purpose) and so it is much easier to remember. These kinds of passwords are much better than a single-phrase password (although only replacing letters with numbers is not secure enough).
Another solution would be to use a password manager that generates and stores unique secure passwords. That way you only have to remember one secure password; the one for your password manager.
If you’re composing the passwords yourself, it's recommended to use at least 8 characters, and include at least one of each of the following:
Never reuse a password you’ve used in the past! The ideal password is unique and hard to guess based on easily accessed information.
Run a strict and clear policy with your user permissions so that only people who really need it can get access to your WordPress dashboard. If you are using managed WordPress hosting or have a large team of designers, editors, SEO managers etc. make sure you understand their roles before giving them permission to make changes to your website.
WordPress has the following user roles and their permissions:
* Themes and plugins can add or remove roles.
A mentioned above, Brute Force attacks are carried out by hackers or bots trying to guess your password. If there's no restriction to the number of failed login attempts, the attacker can keep trying indefinitely until they manage to guess the correct password and access the dashboard.
When you set a limit to the number of failed login attempts before the system automatically blocks the attacker’s IP from accessing the website, you cut these attackers off from your site.
One of the easiest ways to set this up for self-hosted or managed WordPress hosting is using a plugin called Limit Login Attempts Reloaded. It’s available for download from the official WordPress plugin repository.
uPress customers: The plugin WeSafe is installed by default on all the websites on our servers and performs this action.
Two-factor authentication means that everyone logging in has to enter a unique one-time code that the WordPress site sends via email or SMS, or generates on another device. Two-factor authentication can significantly improve website security for your managed WordPress hosting site and provides an extra layer of defense.

DG-Studio / Shutterstock
One of the easier ways to do this for your managed WordPress hosting site is by using the Google Authenticator plugin that's available for download from the official WordPress repository. It offers two-factor authentication via a mobile app.
After installing everything, you log in to your WordPress site with your username and password. You'll be requested to enter a 6 digit code from the mobile app. The code changes every 30 seconds and can be generated only on the app that is paired with your user account.
Please note: In order for this to work, you must have the Authenticator app installed on your smartphone.
When you or your managed WordPress hosting team add or alter anything on your site, the information is transferred from one server to another. Hackers could intercept that information stream and use it to steal data or hack into your site. But a TLS certificate encrypts the data so that if it was intercepted, no hacker would be able to read it.
The TLS certificate is based on unique encryption keys installed on the website’s server. Your computer can only decrypt the information using those encryption keys.
You can acquire a TLS certificate for free with most hosting providers, using Let's Encrypt.
Upress customers: You can install a TLS certificate from the security tab in our management panel.
Data security in self-managed and managed WordPress hosting websites is a sensitive topic that should not be taken lightly, especially when you’re dealing with a website containing sensitive information. Each and every one of the tips and methods mentioned above will take you one step closer to a safe, secure website. When you begin with a secure foundation, you'll find it much easier for you or your managed WordPress hosting team to keep your site secure for the long term.
As managed WordPress hosting experts, we know what we're talking about, whether you need advice on preventative maintenance, ensuring security, or you just want to know what's slowing down your site. You can trust us with the entire gamut of WordPress questions, so the only one left is... why aren't we hosting your WordPress site yet? Click below and join us.


